In this article we will see how to invoke GCP(Google Cloud Platform) Services API's from OIC using JWT Authorization.
We will be utilizing the Service Account from GCP for this purpose. Even though we could utilize the OAuth Authorization Code flow , but for a server to server communication Service Account is preferred approach.
GCP Documentation can be found here : https://developers.google.com/identity/protocols/oauth2/service-account
Prerequisite for this would be to create and download the JSON file for the service account from GCP. The sample JSON looks like this,

Below image gives the high level sequence of steps that should happen in order to generate and utilize an access token.
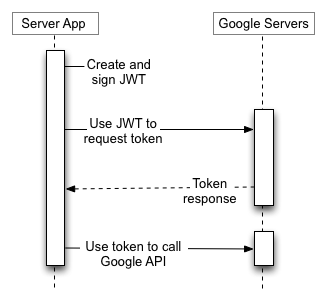
Creating JWT
A JWT is composed of three parts: a header, a claim set, and a signature.
JWT header
Below is the sample JSON for a header. Prepare this and save it in a file called Header.json
alg: fixed to RS256type: fixed to JWTkid: the private key ID of the service account. (refer Service Account's JSON)
{
"alg":"RS256",
"typ":"JWT",
"kid":"<private key ID of the service account : private_key_id>"
}
JWT claim set / Payload
Below is the sample JSON for a payload. Prepare this and save it in a file called Payload.json
iss: The email address of the service account. (refer Service Account's JSON)scope: A space-delimited list of the permissions that the application requests. Check the list here.exp: The expiration time of the assertion in EPOCH. For OIC keep this blank.iat: The time the assertion was issued in EPOCH. For OIC keep this blank.sub: For OIC keep this blank.
{
"iss": "<The email address of the service account : client_email>",
"scope": "https://www.googleapis.com/auth/cloud-platform",
"aud": "https://oauth2.googleapis.com/token",
"exp": "",
"iat": "",
"sub" : ""
}
Signature
We can extract the signature from Service Account's JSON. Fetch the private_key and store it in a new file. This will be uploaded to OIC's certificate page.
Note : Make sure to remove all the \n string from the private key string and replace the same with actual new line.
The final file should looks like this,

Configurations in OIC
Upload the Private Key Certificate
Login to OIC
Navigate to Settings -> Certificates
Click on Upload
Give an "Alias Name". This will later be used in OIC Connection.
Select Type as "Signing key"
Set the Category to "Private"
Choose the Signature/Private Key File which we we prepared in previous step.
Click on Upload

Create a OIC Connection
Let us create a REST connection. Go to the connections page and choose REST Adapter to create a new connection.
Connection Type : REST API Base URL
Connection URL : Base URL of the actual API which you will be invoking. This could be API for any service in GCP. Make sure the Service Account created has access to that Service.
Security Policy : OAuth using JWT User Assertion
Access Token URI : https://oauth2.googleapis.com/token
JWT Header : Upload the Header.json prepared above
JWT Payload : Upload the Payload.json prepared above
JWT Private Key Alias : Specify the Alias Name which we used while uploading the Private Key.
Access Token Request : Under the Optional security specify the below value.
-X POST -H "Content-Type: application/x-www-form-urlencoded" -d 'grant_type=urn:ietf:params:oauth:grant-type:jwt-bearer&assertion=${user_assertion}' ${access_token_uri}

You are all set !!. Test and Save this connection and utilize it in any OIC flows.

